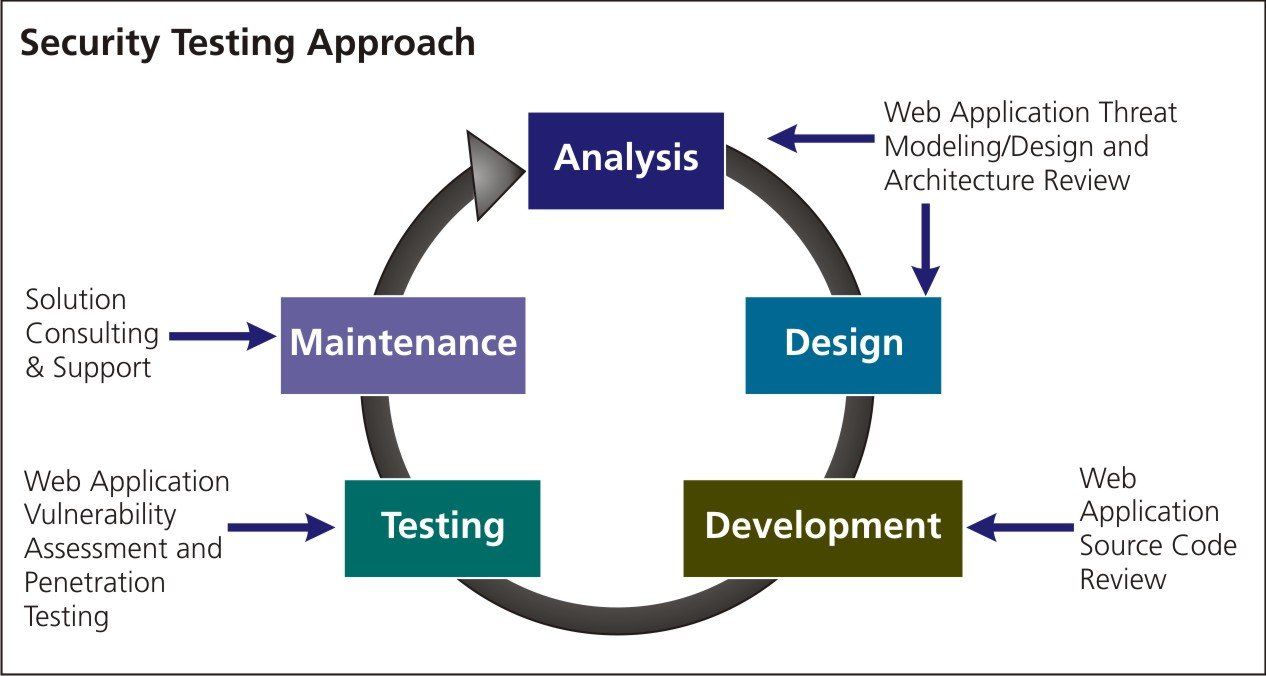
Penetration testing tools and techniques


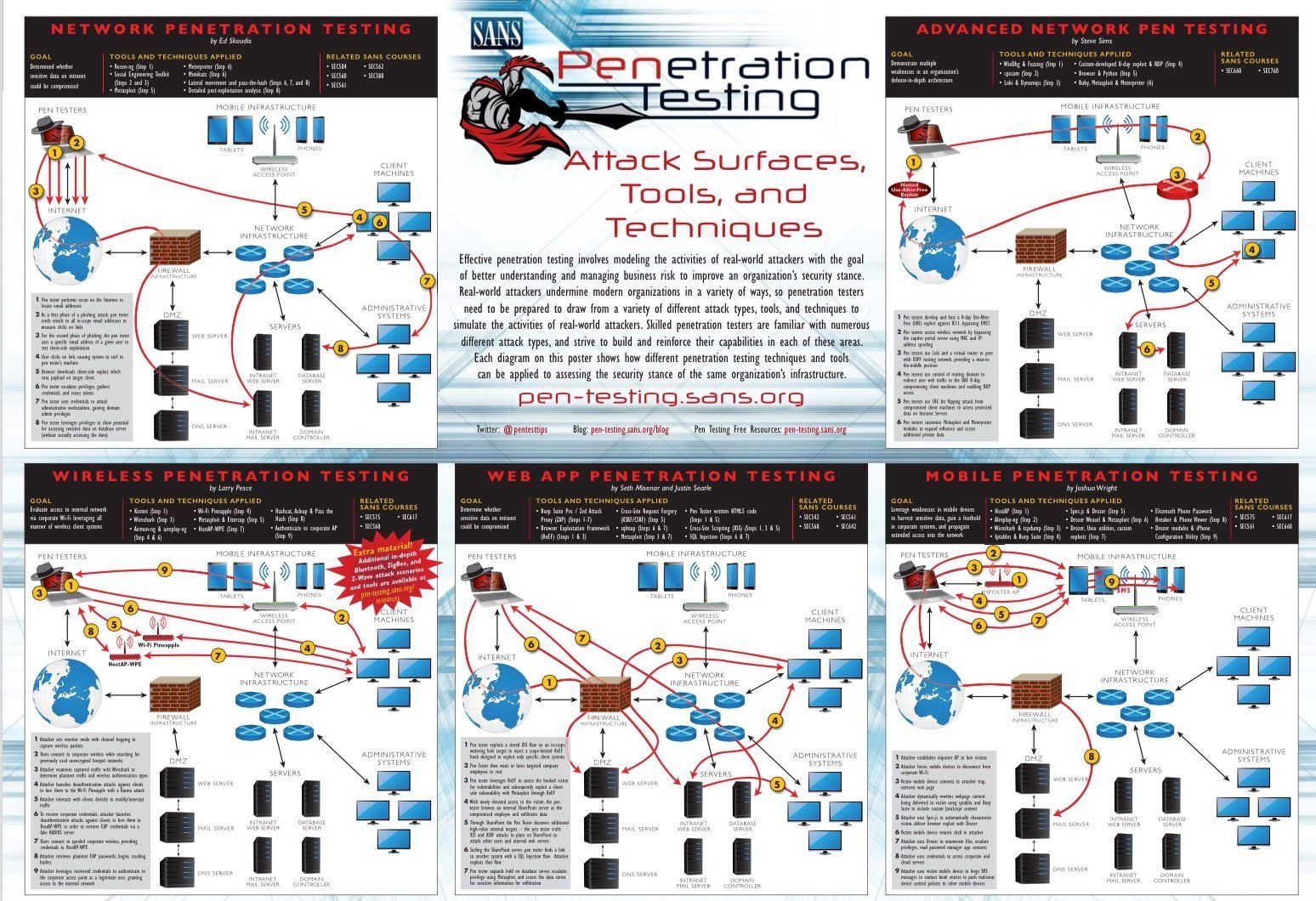
Penetration testing is designed to assess your security before an attacker does. Penetration testing tools simulate real-world attack scenarios to discover and.
Penetration Testing

I Eunice Age: 35. I am a pleasing companion for all of my gentlemen friends.Services completes, active passive, sans tabous, blonde, tres cambree, bronzee, et tres femenine

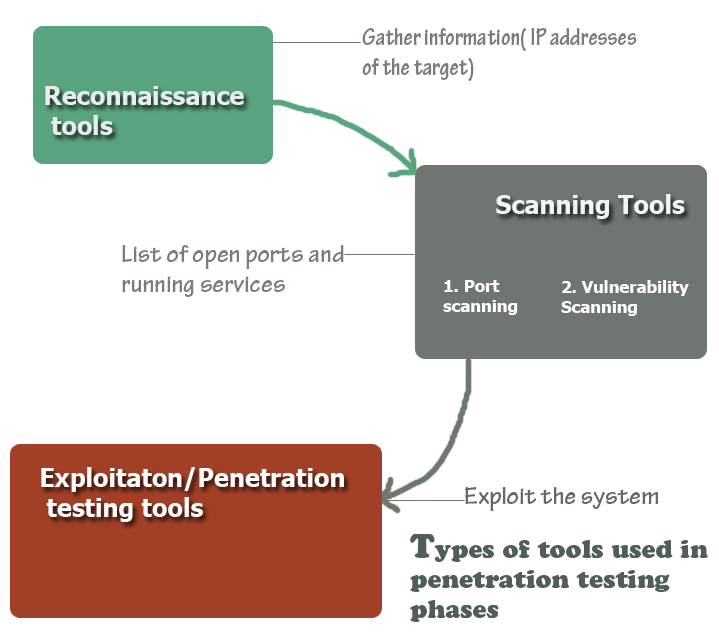
Penetration testing techniques -- Chapter 6, Professional Pen Testing for Web Applications


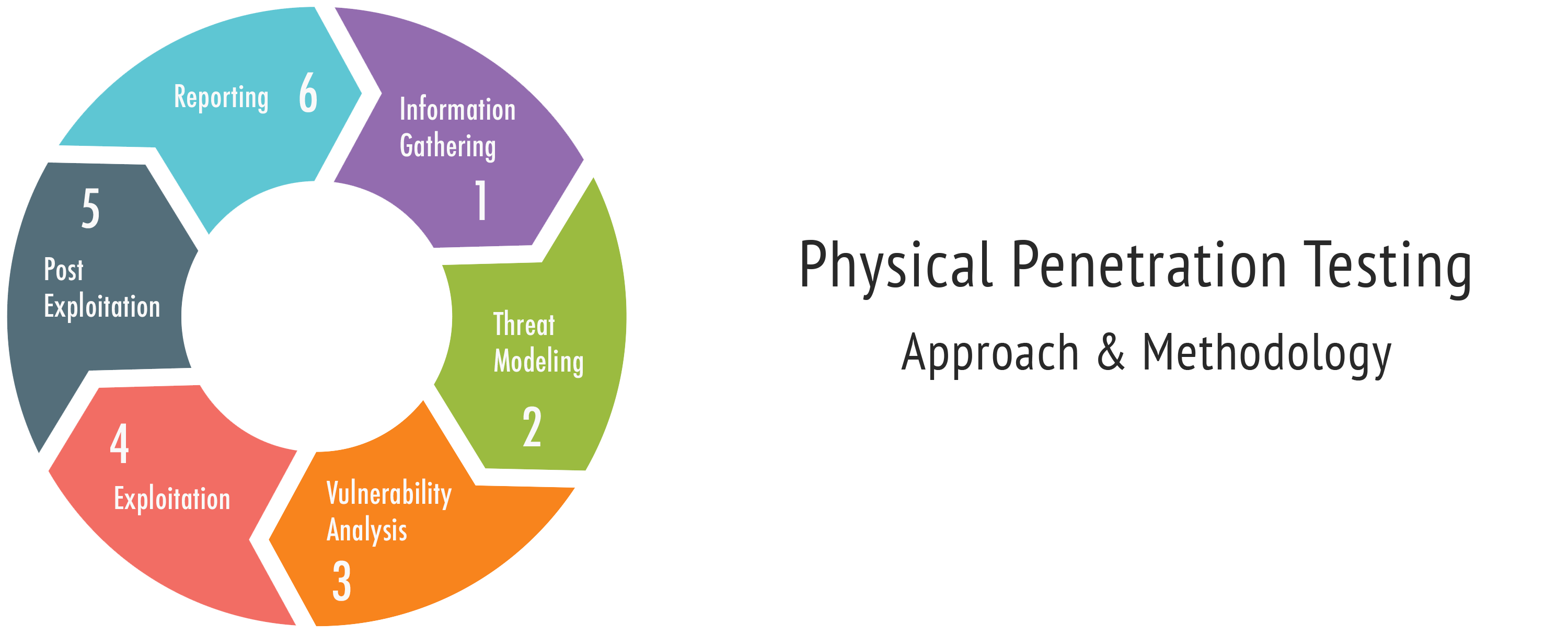


Uncover security gaps before attackers do


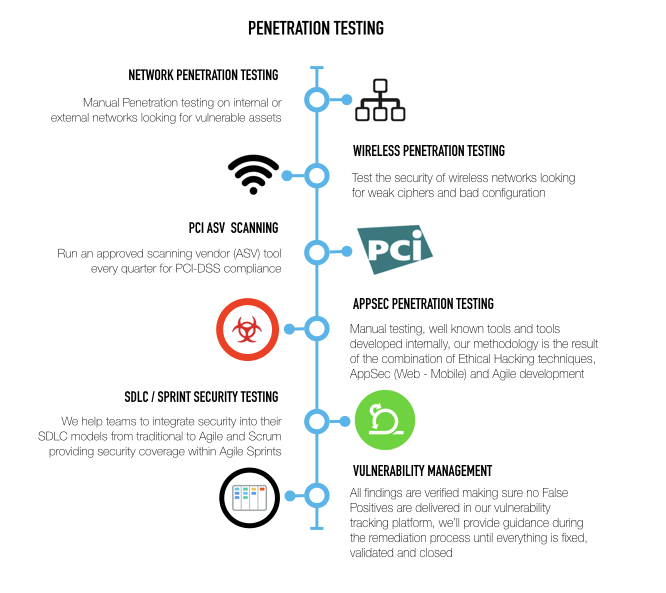

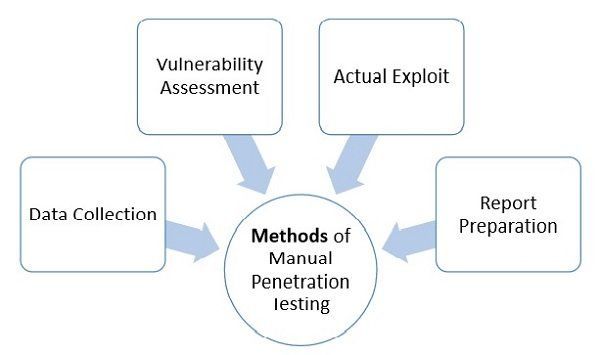
Want to find a partner you like Penetration? Find
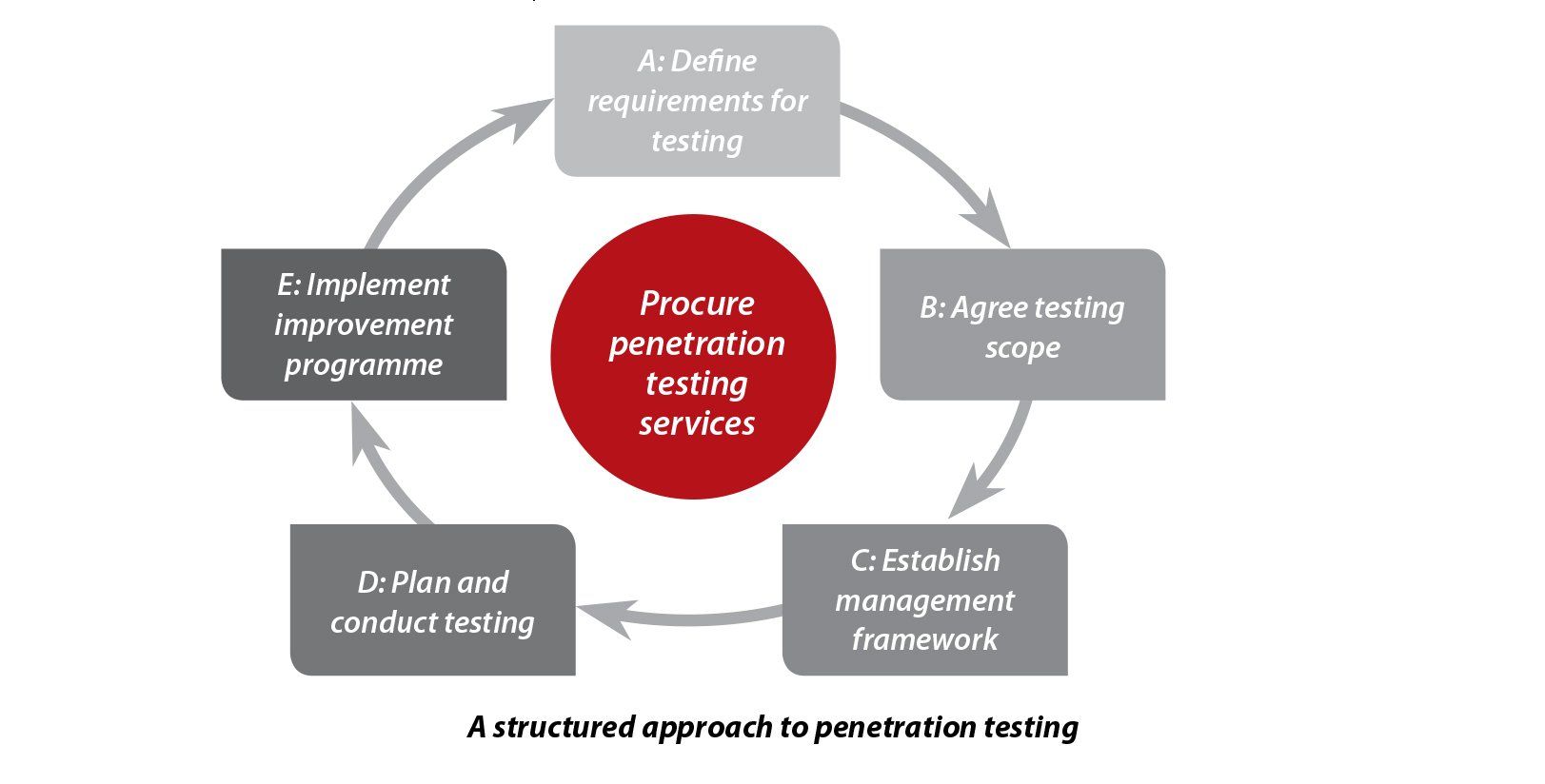

This course, updated for , covers the various tools, techniques and procedures penetration testers use to test systems and networks of systems for.
Description:There is no such thing as "perfect security" when it comes to keeping all systems intact and functioning properly. You can download the source code directly from Bitbucket at this page. The penetration tester too must develop detailed reports to explain each step in the hacking process, vulnerabilities exploited, and systems that were actually compromised. This made the use of wordlists vital versus other methods.




































User Comments 5
Post a comment
Comment: